APT40
Who is TEMP.Periscope?
TEMP.Periscope, also known as Leviathan, TEMP.Jumpter, and APT40 is likely a Chinese, state-sponsored group that has focused its efforts on engineering and maritime industries, especially entities connected to issues involving the South China Sea. Some of the engineering organizations include research and academic institutions as well as private engineering firms in the United States. FireEye describes this group as having been active since 2013 and most recently in March 2019. [4][5]
FireEye attributed attacks against Cambodian elections to APT40. These compromises occurred before Cambodian elections on July 29, 2018.
FireEye listed a group of compromised Cambodian organizations.
- National Election Commission, Ministry of the Interior, Ministry of Foreign Affairs and International Cooperation, Cambodian Senate, Ministry of Economics and Finance
- Member of Parliament representing Cambodia National Rescue Party
- Multiple Cambodians advocating human rights and democracy who have written critically of the current ruling party
- Two Cambodian diplomats serving overseas
- Multiple Cambodian media entities
TEMP.Periscope compromised a "European chemical company with in Asia", according to FireEye. This reveals a world-wide scope of targets with organizations related to Chinese interests. [6]
As of March 4, 2019, FireEye reported their discovery of attacks targeting "countries strategically important to the Belt and Road Initiative including Cambodia, Belgium, Germany, Hong Kong, Philippines, Malaysia, Norway, Saudi Arabia, Switzerland, the United States, and the United Kingdom." [3] FireEye believes APT40 has focused on strategic maritime targets to support China's plans to establish a competitive navy.
On March 5, 2019, the Wall Street Journal was quoted by multiple news outlets saying at least 27 different universities in the US, Canada, and Southeast Asia have been targeted by TEMP.Periscope including "University of Hawaii, Massachusetts Institute of Technology (MIT) and the University of Washington", among others. [1]
Aliases
- APT40
- Leviathan
- Mudcarp
- TEMP.Jumper
Notable Attacks
- Cambodian government
- US organizations focused on maritime research
- Organizations world-wide relating to the South China Sea
Victims
- At least 27 different universities in the United States, Canada, and Southeast Asia have been targeted by the attackers including the University of Hawaii, Massachusetts Institute of Technology (MIT) and the University of Washington. [1]
- Victims closely related to the Belt and Road Initiative including Cambodia, Belgium, Germany, Hong Kong, Philippines, Malaysia, Norway, Saudi Arabia, Switzerland, the United States, and the United Kingdom.
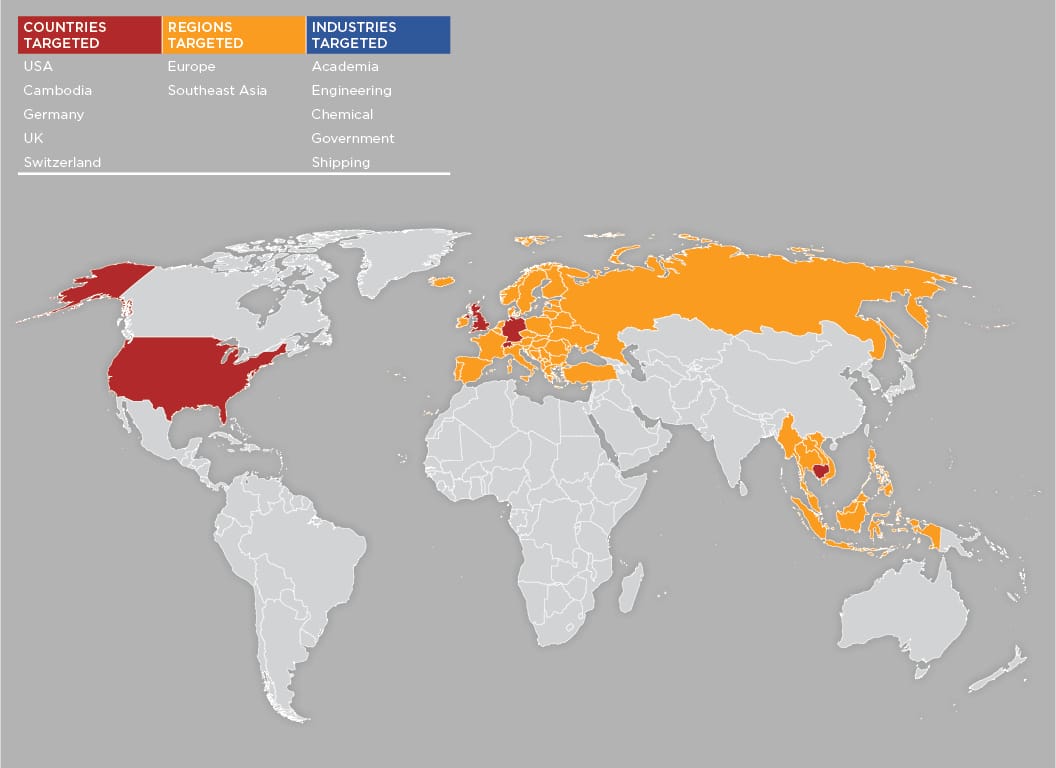
Image 1 Summary of APT40 activity locations. [6]
Tactics
APT40 acts on all phases of the attack lifecycle. They usually begin by delivering payloads through phishing and complete their attack through exfiltration and ongoing persistence. FireEye notes that APT40 will often target VPN and remote desktop, because access gained there will reduce the likelihood of needing to rely on malware and phishing.
These attackers typically reuse existing toolsets they made custom or simply use open source tools with minimal modification. Infrastructure retooling does not appear to be a significant hurdle, as the group appears to already have access to proxy machines gained through previous attacks or will quickly find new victim C2s. In either case, APT40 does not need more than a few weeks to begin a turnaround on a new campaign.
TEMP.Periscope compromises victims primarily through spear-phishing which include malicious attachments or Google Drive links. To be successful, the attackers must understand their victims' interests and current events. This group will most often send an infected decoy document which relies on providing the victim with an interesting topic to get them to open the malicious document.
The documents contain a malware down-loader that begins downloading the malicious payload then redirect the victim to the legitimate source of requested content. TEMP.Periscope often uses exploits for newly discovered vulnerabilities and will compromise web servers to gain an initial foothold into a victim's network. Examples of vulnerabilities APT40 developed exploits for include CVE-2012-0158, CVE-2017-0199, CVE-2017-8759, CVE-2017-11882.
Once TEMP.Periscope gains access to a network, they establish persistence using backdoors, VPNs, and remote desktop, leveraging Hyperhost VPS and Proton VPN exit nodes to access webshells on internet-facing systems. The attackers will then escalate privileges and dump user credentials. With the captured credentials, the group will scan for other machines and move laterally across the network to perform recon and steal additional information. TEMP.Periscope favors webshells or other publicly available tools for long-term access to these networks and continues to extract data.
Two of the C2 domains used in the attacks against Cambodia were chemscalere.com and scsnewstoday.com. Another domain, mlcdailynews.com, was used by the SCANBOX malware. FireEye discovered logs on the C2 servers which included information about an IP address in Hainan, China that was used to configure the C2 servers and control malware on victim machines. These logs also included C2 check-ins from victim machines.
NOTE: Some of the security vendors incorrectly classified the code in NanHaiShu as JavaScript. The actual technology is JScript with is a Microsoft-based scripting language similar to JavaScript but can execute with less restrictions and has access to .NET APIs. JScript executes with wscript.exe and can run outside of a web browser. This misunderstanding of JScript is common and easy to fall into, but it also demonstrates the attackers advanced knowledge of technology and exploiting software. Such a deep technical understanding is uncommon.
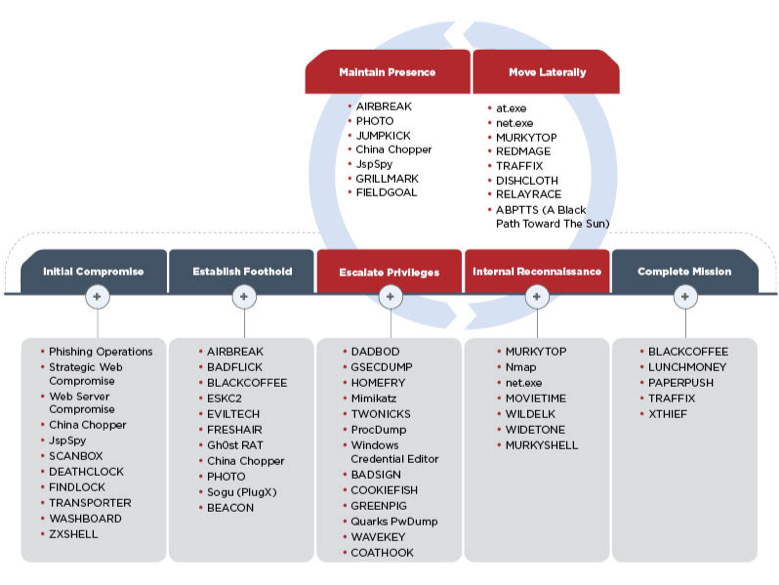
Image 2 Tools used during attack life cycle [3]
Tools used during various attack stages
Initial Compromise
- Phishing
- Strategic web compromise
- Direct web server compromise
- China Chopper
- JspSpy
- SCANBOX
- DEATHCLOCK
- FINDLOCK
- TRANSPORTER
- WASHBOARD
- ZXSHELL
Establish Foothold
- AIRBREAK
- BADFLICK
- BLACKCOFFEE
- ESKC2
- EVILTECH
- FRESHAIR
- Gh0st RAT
- China Chopper
- PHOTO
- Sogu (PlugX)
- BEACON
Escalate Privileges
- DADBOD
- GSECDUMP
- HOMEFRY
- Mimikatz
- TWONICKS
- ProcDump
- Windows Credential Editor
- BADSIGN
- COOKIEFISH
- GREENPIG
- Quarks PwDump
- WAVEKEY
- COATHOOK
Internal Reconnaissance
- MURKEYTOP
- Nmap
- net.exe
- MOVIETIME
- WILDELK
- WIDETONE
- MURKYSHELL
Exfiltration
- BLACKCOFFEE - Used by APT17 and other Chinese cyber espionage operators.
- LUNCHMONEY
- PAPERPUSH
- TRAFFIX
- XTHIEF
Move Laterally
- at.exe
- net.exe
- MURKYTOP
- REDMAGE
- TRAFFIX
- DISHCLOTH
- RELAYRACE
- ABPTTS
References
[2] https://otx.alienvault.com/pulse/5589f402b45ff578e825e6f2
[5] https://www.f-secure.com/documents/996508/1030745/nanhaishu_whitepaper.pdf
[8] https://www.recordedfuture.com/chinese-threat-actor-tempperiscope/
